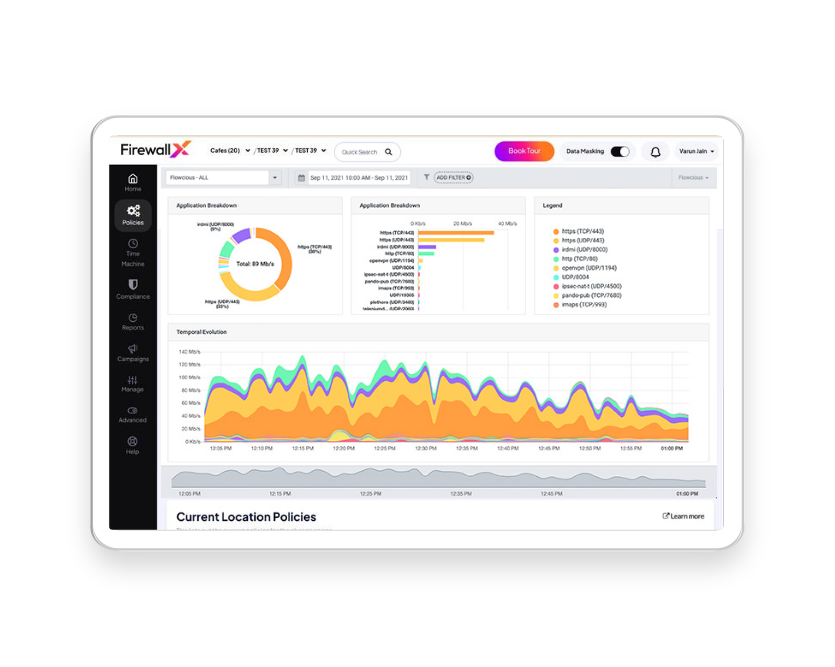
FirewallX Visibility gives you real-time insights into users, traffic, and threats — without DPI or complex tools. Get the answers you need in minutes, not hours.

Lean IT teams are now responsible for securing more users, devices, and environments

of cyberattacks now target Small and Mid-sized Businesses

of SMBs hit by a cyberattack shut down within 6 months

is the average cost of a data breach for an SMB
Across SaaS, HealthTech and Education


















































Not just visibility — the context, clarity, and coverage your IT team needs to act with confidence.
Spot lateral movement, DDoS, exfiltration, and other threats instantly using AI and behavioral models — no DPI required.
Enrich flows with IAM, device metadata, and login data to answer “who did what, where, and when” — instantly.

Track shadow IT, policy drift, and compliance anomalies (GDPR, DPDPA) with forensic logs and ready-to-export reports.
Ditch dashboards — just ask. Get answers, alerts, and actions in plain English via a ChatGPT-style interface.
Stream and enrich data from your firewall, access points, syslogs, IAM, and more — all stitched into
one AI-powered engine for real-time insights, alerts, and compliance mapping.
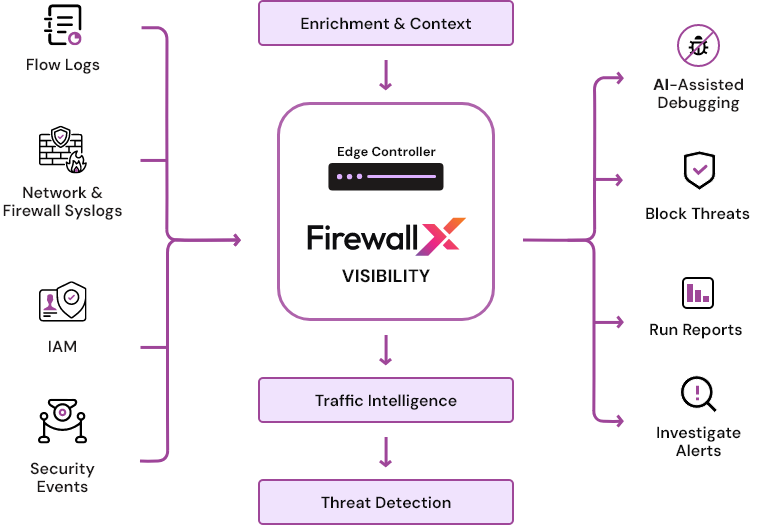
FirewallX Visibility turns blind spots into action — helping you detect threats early,
enforce policies, and meet compliance without more tools or effort.
Stay ahead of lateral movement, insider misuse, and evolving threats — without drowning in false positives.


Know exactly who did what — across every device, app, and location.


Make audits stress-free and stay ahead of policy violations — no spreadsheets needed.


Stay Ahead of Issues — With Proactive Monitoring & Alerts


Discover stories of businesses that overcame challenges and achieved remarkable results thanks to our tailored and collaborative approach.
 Coworking
Coworking
Learn how a fast-growing coworking company strengthened network security and increased member satisfaction by 45% cloud-managed platform — cutting IT support tickets by 70% and freeing up lean IT teams
 Saas/Tech
Saas/Tech
See how a fast-growing SaaS company unified secure access, threat protection, and compliance — cutting downtime, boosting team productivity, and passing critical audits effortlessly.
 Education
Education
See how a leading university safeguarded student and staff internet access, cut bandwidth misuse by 40%, and stayed audit-ready — all managed effortlessly identity-based controls.
 Healthcare
Healthcare
Discover how a growing multi-clinic healthcare provider secured patient data, ensured 99.9% network uptime, and simplified HIPAA compliance — all without expanding their IT team.
 Retail
Retail
Learn how a national retail brand protected PoS and guest networks, boosted uptime by 60% across stores, and simplified IT operations with FirewallX’s centralized, cloud-managed security platform.
You’re not alone. Let’s talk about what’s not working — and whether FirewallX is the right fit to simplify your network, security, and compliance. No pressure. Just clarity.
Book a Demo